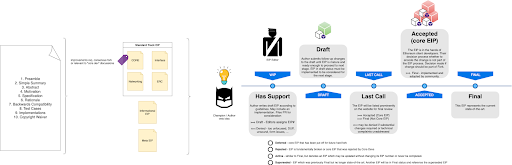
Diving deep into Audit Contests Analytics and Economics
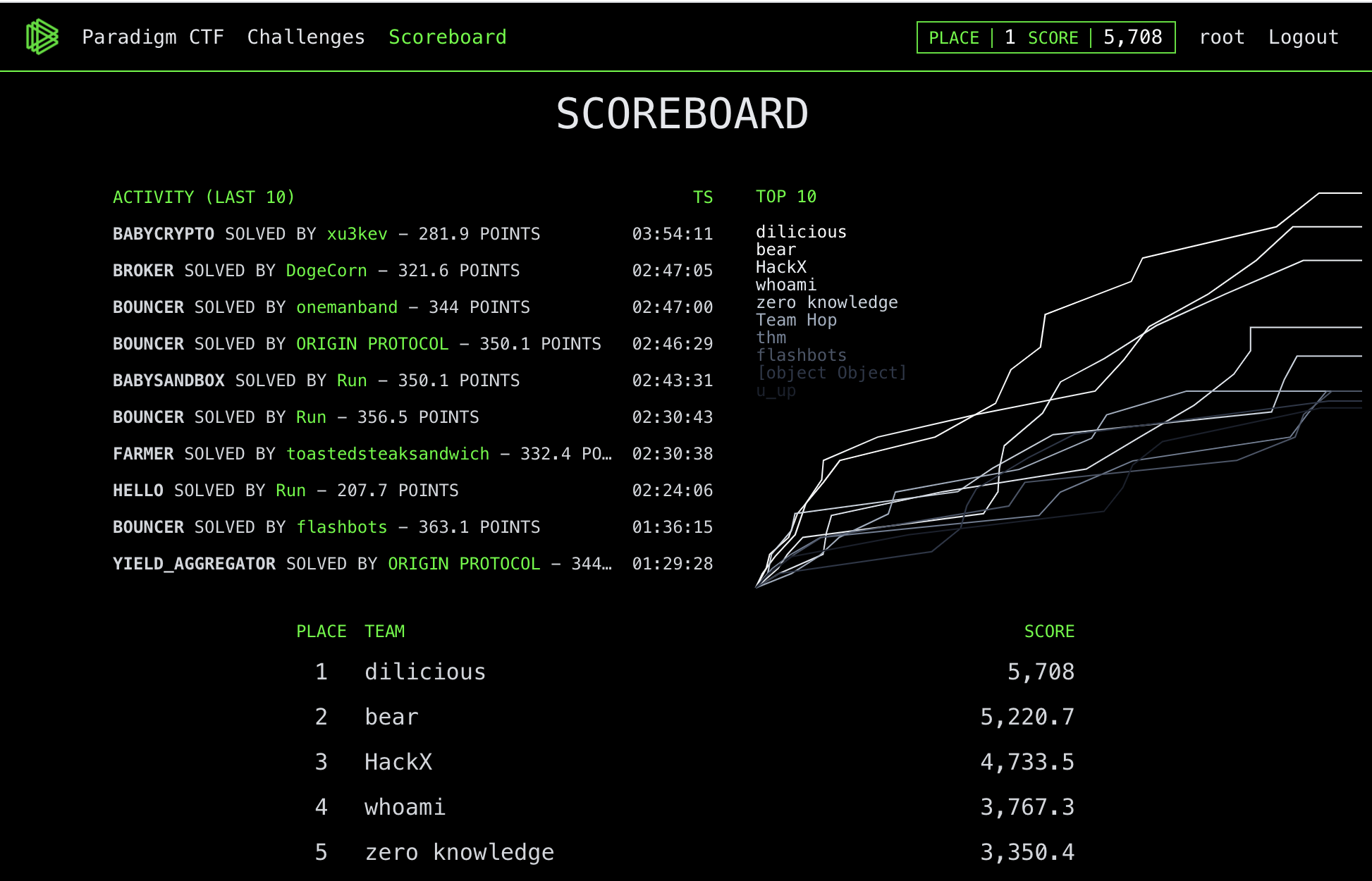
It’s been a couple of years since code4rena has introduced competitive audits into the smart contract security landscape, and it looks like audit contests are here to stay. In the meanwhile several other platforms have popped up with the same forumula.
Audit contests are simple. A project publishes a set of smart contracts that they would like to have audited, and promises a prize pool for security related findings. A contest is ran for a couple of weeks during which participants can submit their findings.
Joran Honig
April 12, 2024